This article is intended to provide an introduction to the topic of 'side-channel attacks' on ICs and outline techniques that are sometimes used by professional attackers with surprisingly little effort.
Design and data security is also increasingly being recognized as an issue in the industry. The preliminary essence of countless discussions is: "We could do more in this area." The positive aspect of this statement is that the topic is known and there is an awareness of it. The negative aspect of the same sentence is the use of the subjunctive mood. It expresses the fact that only a few companies are seriously or sufficiently concerned with the topic.
Why design and data security is important
From countless use cases, the following three should serve as a representative illustration. First example: Development and innovation cost time and effort. This is an important investment for a manufacturing company. Customers associate a level of quality and reliability with the manufacturer's products. If an imitator comes up with the idea of copying the product, it is initially relatively easy to identify the right components and copy the circuit board. The memory contents are then quickly copied from the original and the competitor's product is ready - with almost no effort at all. This means it can also be offered more cheaply on the market and customers will buy and use it.
If there is now a warranty claim, the customer using the product goes to the supposed original manufacturer and ... is not known. Now it must be proven that the manufacturer of this special card is not the original manufacturer. Without implemented 'security', the original manufacturer risks losing sales to copiers, exposes itself to unjustified warranty claims and risks its good reputation on the market.
A second example of a security-critical application: the gate control system of a dam is attacked. The attacker now opens and closes the gate at his own discretion. The consequences can range from disastrous to fatal. The aim should be to prevent under all circumstances that only permissible and intended algorithms can run on the control hardware, which may also have to comply with applicable functional safety guidelines.
One last example from the daily life of every driver: speed measuring devices are scattered all over the country at the side of the road. Someone could come up with the idea of modifying the measurements in one direction or another. The personal annoyance would be great if unjustified penalty notices were received for speeding. Who would accept the fines or points?
 The consequences of an attack on the control hardware of a hydroelectric power plant are unimaginable; Image: AdobeStock
The consequences of an attack on the control hardware of a hydroelectric power plant are unimaginable; Image: AdobeStock
Types of attacks
In principle, possible attacks on the hardware can be divided into different groups, which differ according to the attacker's prior knowledge of the target. Black-box, grey-box and white-box are used here for the following explanations.
In a black-box attack, the attacker initially has no information about what is happening in the chip. He identifies inputs and outputs, observes them and draws conclusions about the inner workings - the design or program. To create a product copy, as in the first example, not much more is needed. The flash contents are read out and copied to identical hardware. That's it. However, if the attacker's goal is to obtain the contained algorithms, a little more effort is required and this is greater in the black box case than in the other two. But one thing is certain: it is only a matter of time and therefore effort before the design is no longer a secret. The crucial point is how much energy and therefore money the attacker is prepared to invest. This is now a matter of judgment. Different standards are applied to toys than to gate control systems for dams or communication equipment for governments.
In the case of a grey box attack, the attacker has the same knowledge as in the black box scenario, but also 'sees' input (= output from the IC's point of view) of parasitic information. This information originates from the technical implementation of the desired functions and any security mechanisms. Why are passwords not displayed when they are entered in login screens? Of course, someone could hide in front of the window and try to catch the characteristic signal of the radiated screen display with an antenna and thus identify the password. The same principle can also be used for ICs. Typical mechanisms are the analysis of power consumption, electromagnetic radiation, photon emission or simply the time a given task takes to complete. These types of attack will be explained in more detail shortly.
Whichever method is used, the attacker gains additional information about the design and can draw increasingly precise conclusions with the help of statistics. Of particular interest is the master key of any encryption, which should always be used as minimum protection. Once this is known, the rest is just optional.
In a white box attack, the attacker has full knowledge of the inner workings and implementation of the security function(s). It is therefore less of a classic attack and more of a necessary step in the design phase. Just as firmware developers simulate their software to ensure correct functionality under all circumstances, a development team, or even an external service provider, attempts to provide the development team with information about possible weak points through test attacks.
Cryptography is a recognized efficient method of protecting design and data from unwanted access or manipulation. The mathematical methods used are sophisticated and secure per se according to the current state of the art. This is where these two factors come into play: 'the state of the art' and the encryption algorithm.
The former is, of course, constantly evolving. New standards are necessary in order to meet future security requirements, even with increasingly powerful computing capacities for carrying out attacks. The keyword 'quantum computer' is just one of many that come to mind here. This means that encryption that is considered secure today - because attacks requiring many years of computing time are necessary - may be little more than a minor obstacle in a few years' time. Since commercial products are expected to achieve a certain lifetime on the market, a security solution must incorporate these trends into the architecture and its implementation. In other words, it is not enough for the solution to correspond to the current state of the art. It must also be sufficient for the duration of the product's distribution and operation.
One way of meeting changing requirements is to enable product updates. The advantage is obvious: the product can be adapted over time and any weaknesses can be rectified. However, this also gives an attacker an additional opportunity for an attack. He only needs to install his own update instead of the intended one. It is therefore essential to ensure that only authorized, authenticated updates can be installed. With more powerful computers, older cryptographic algorithms are easier to 'crack'. This makes it necessary to further develop the algorithms and, in most cases, the length of the key. The challenge lies in not restricting the actual function too much by implementing the security. Given computing power can be used for the security function or the application. An efficient implementation of cryptographic algorithms is therefore essential. This brings us to an important point: the technical implementation of the algorithms. In hardware, this is realized at transistor level. These switching elements are charged and discharged, which requires energy. This takes time and leads to the emission of electromagnetic radiation or photons. These side effects can be recorded and used for analysis by an attacker after statistical considerations. These are classic side-channel attacks. The important thing is: It is not the algorithm that leads to these information leaks, but the actual implementation in the computer.
Let's take a look at the sidechannel attacks that have already been mentioned repeatedly.
Execution times of queries for true or false inputs are one method of attack. The idea is to trigger the cryptographic function in the 'protected circuit'. Example: Access authorization to the apartment building. In the simplest case, a fixed setpoint is stored as an access code in the controller at the front door of the block of flats. Each time one of the characters is entered via the keypad, an immediate query is made as to whether the entry corresponds to the setpoint. If this is the case, the next entry is evaluated. If the wrong key was pressed, the process is aborted. The two paths of the query will usually require a different time for processing in the controller. This can be measured using the power consumption profile, for example.
It is more or less easy to manipulate this evaluation time as a developer so that it is the same in all cases or only a complete input is generally evaluated or ... At this point, the developer has already thought about a secure implementation. He is one step further than with the implementation of pure and simple functionality.
The absolute or relative power consumption of circuits can be determined in different ways. Current measurement via shunt resistors is the key. The challenge for the attacker is now to relate the observed current or power profile (after multiplication with the voltage) to known actions. Such a known action can be a triggered crypto function, for example. The statistical evaluations already mentioned several times again help to identify the exact time of encryption and thus, sooner or later, the key.
The measurement of the electromagnetic radiation emitted can be recorded via antennas and evaluated again. The procedure is essentially the same as for measuring power consumption. The main difference is that the power consumption refers to the entire chip, while the determination of the radiation as a function of the antenna size and shape can be very fine-grained. This makes it possible to generate an activity map of the chip, a kind of map for the attacker. The relevant areas are then closely monitored and series of measurements are carried out. At the end, the statistical evaluation takes place again.
During the operation of ICs, photons are also released in the active area. If these are counted using appropriate measuring devices, an activity map can also be generated in this way. The remaining steps are identical to the other methods.
The methods mentioned for side-channel attacks all have their strengths and weaknesses. In particular, they involve different costs. The question of the effort to be made by the attacker therefore arises when choosing the means. To give you an idea: For a demo seen to determine the AES key of an unprotected microcontroller, equipment worth about $500 was used. This was an antenna for about $20 and a simple oscilloscope. The standard PC used for the calculations is not included. The antennas for more sophisticated attacks are sometimes in the three- or four-digit range. The same applies in principle to oscilloscopes. There are hardly any upper price limits. The data volumes involved range from a few MB to several TB. Some of the necessary software is even available as open source code.
In addition to pure 'eavesdropping', attackers also have the option of actively manipulating the circuits in order to provoke deliberate and targeted reactions. For example, local changes in temperature can lead to runtime-related errors in the cryptographic algorithm and be used to analyze the key. Power glitches, brownouts or even clock glitches can cause ICs to enter unstable and undefined states. The same is also possible with electromagnetic radiation and laser light. Essentially the same physical methods that were previously used for measurements are now being used to actively influence and disrupt ICs in order to gain new insights.
Many analysis methods for extracting crypto keys have the word 'power' in their name: Simple Power Analysis (SPA), Differential Power Analysis (DPA), Correlation Power Analysis (CPA), Mutual Information Analysis (MIA), Linear Regression Analysis (LRA), Template Attacks, ... Even if the term 'power' is used here literally, the method is not limited to analyzing power alone, but can also be applied to other physical variables.
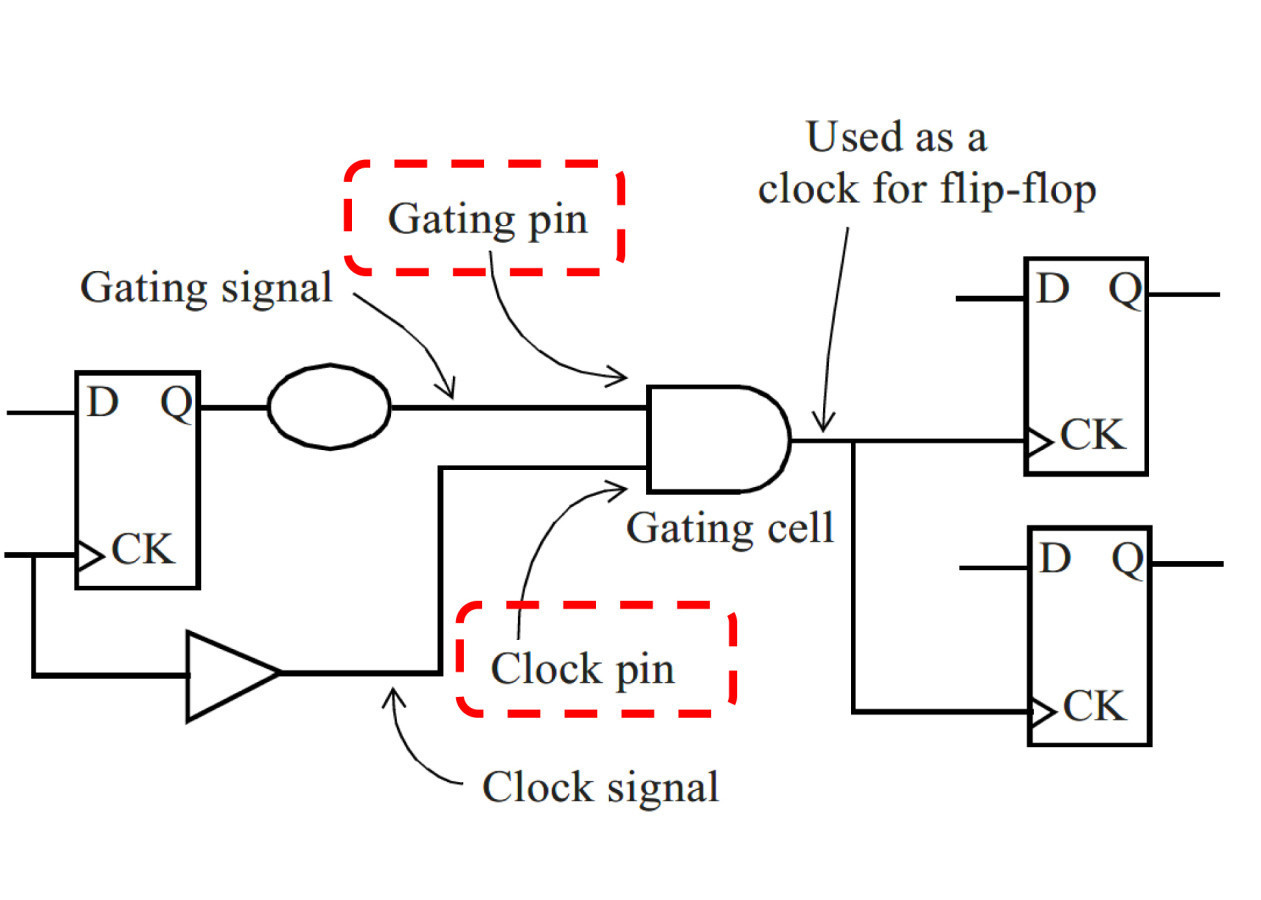 Clock gating check; Image: Southwest Jiatong University
Clock gating check; Image: Southwest Jiatong University
Conclusion
There can be no such thing as 100 % certainty. It is therefore also pointless to protect a circuit or application against all types of attack. The security objective and the attack scenario to be prevented must be clearly and realistically defined from the beginning of the design cycle in order to be implemented efficiently.
The biggest obstacle to the widespread effective use of security mechanisms is probably the fact that the additional work involved in the form of development time and the associated product costs usually do not provide the end customer with any direct added value in terms of features. The added value appears to lie on the manufacturer's side in particular. In connection with time-to-market and a margin necessary for the continued existence of the company, design and data security often suffers according to the current state of affairs and is sometimes optimized away or implemented so poorly that it can almost be classified as non-existent.


